Method 1: Crack Windows Vista Password without Reset Disk or Software. When you install Windows Vista on your computer for the first time, you have to create a new user account which has the highest privileges in the computer and once you create it, Windows setup automatically disables the user account and you can't log on it in normal mode but in Safe Mode. Easy to use; passwords are recovered automatically. Doesn't require installation; it runs.
Hack Vista..
Locked out of Windows Vista? XP? NT? Overwrite the administrator password or any user password with a boot disk called Trinity Rescue Kit. All you gotta do is download this .iso with your computer, and copy it to a cd or dvd with ImgBurn.
Once done put cd back in, and restart the computer or put this disk in any computer and boot up with it, wait for the linux os to finish booting from cd, you will get a prompt, type “winpass” press enter
it is mounting the drives for windows, you can choose which os if you multiboot..
In most cases all you do is press enter if you only have one os.
Enter “*” for blank administrator password or enter whatever you need, confirm with y then enter.
Password changed 🙂
This shouldnt take anyone more than 5 minutes to do…
Hack Vista Password Without Cd
You can also change any username with winpass -u “username”
easy as that.
Enjoy 🙂
Download ISO to reset administrator password Here
Vista Hack Passwords
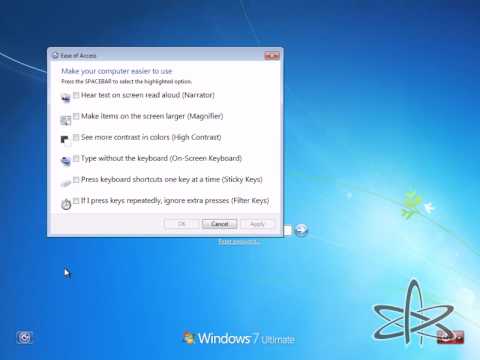
Vista Hack Password Manager
Winpass
By default it will reset the builtin administrator account of a locally installed Windows, but you can specify other accounts as well at the commandline. In fact, you can add any parameter from chntpw which will be parsed to the commandline. So winpass –l will list you all usernames found in the SAM. Should you have troubles that metacharacters are present in the username (like the Ø or something), you can still use the HEX reference to the username listed next to it. Be sure to prepend that with a ‘0x’. More info on that can be found in the manual of chntpw. Watch out with disabling syskey! Most of the time you don ‘t need to disable syskey. It removes strong password encryption, so all local passwords become invalid, since the hashes don ‘t correspond to the encryption algorythm anymore.